Fuzzy-Based Energy Management System With Decision Tree Algorithm for Power Security System
- DOI
- 10.2991/ijcis.d.191016.001How to use a DOI?
- Keywords
- Energy security; Power security service; Incursion detection system; Artificial neural network
- Abstract
Energy security (ES) has great impact on power grids. Therefore it is important to have power security service (PSS). The PSS should be designed to handle interference and interruption attack in the grid. The interference and interruption attack in the grid is handled by incursion-detection system (IDS). The IDS is the most obtainable strategy to sense and classify different security issues and abnormal issues that occur in power grids. Therefore the IDS have to be up to date with the latest issues that happened in the entire grid. The proposed concept illustrate the collection of data with reference to intrude-attacks in power-grid and to test and evaluate different machine-learning strategy to illustrate the different attacks and issues that happen in power system grid. The research work is illustrated with a modified J48 decision tree algorithm.
- Copyright
- © 2019 The Authors. Published by Atlantis Press SARL.
- Open Access
- This is an open access article distributed under the CC BY-NC 4.0 license (http://creativecommons.org/licenses/by-nc/4.0/).
1. INTRODUCTION
Incursion-detection system (IDS) combine both software and hardware to distinguish assaults on power-network to guarantee the security of the framework from unapproved access. IDS can be isolated into two fundamental characterizations dependent on the assault's recognition strategy. The initial one is the abuse, and the second is peculiarity location. The peculiarity location can be utilized in various courses all together to recognize any abnormal conduct of the client inside the system traffic.
An Incursion Detection (ID) based on artificial neural network (ANN) and fluffy grouping (FG) has been proposed to discover a few systems issues and assaults in power-grid. However there are some cons of the proposed model; for instance, it has an absence of precision in low frequent assaults. To overcome the specified cons the researchers divides the heterogeneous training sets into homogeneous training sets. The difficulty in each of the identified is taken into consideration and the complexity is reduced in the training set so as to improve the performance of the assaults detection and the back-up of the complete system is taken completely by using restore points [1]. To be more accurate and efficient in facing the troubles and issues faced in power-grid artificial-intelligence with heuristic and ANN algorithm in IDS to improve the reliability and stability in the learning and development environment. Heuristic combined with ANN approach in IDS gives extra performance with more accuracy [2]. In [3] the user action as a parameter in irregularity is detected in this test by using back proliferation algorithm. The back proliferation algorithm is the most promising technology as the classification rate is 100% while the detection rate is 88% for the known and unknown attacks. This method takes the advantage of utilizing the minimum amount of training data and produces better performance and result in heavy data traffic. An ANN with multilayer perceptron (M-LP) in IDS is considered as more efficient and accurate in terms of detection and normal communication [4]. The use of M-LP limits the detection under low-frequency ass assaults [5]. In the classifier choice model exhibited by Nguyen and Choi [6], they removed 49,596 cases of KDD dataset and compared the set of classifier under the controlled environment. The exhibited various ways to deal with arrangement with KDD dataset, administered, and unsupervised strategies recreated utilizing MATLAB and the researchers test is done with supervised and unsupervised with the framed fuzzy rules to investigate the performance of the complete system. Search algorithm is proposed in [7] between the tree predictors and research proposed error to focus on random-forest. [8–10] Outlined in choice tree analysis on j48 procedure and how it is critical to compute entropy and data gain for every trait in any dataset prepared to be characterized, they utilized optimal tree with univariate and multivariate techniques, additionally the scientists exhibited multivariate technique as straight machine strategy. The specialists suggested this methodology for huge measure of information. [11–15] expressed that nature of dataset once in a while makes it hard to choose fitting credits to learn, and the researchers explores different avenues regarding Naïve Bayes classifier and measure execution for each call.
2. RENEWABLE ENERGY SYSTEM DESCRIPTION
The optimal renewable system configuration shown in Figure 1 represent the dynamic regulation model and this is used to feed power to various types of customers using different types of loads. The renewable grid uses solar for generating power under varying atmospheric condition such as variation in irradiance, temperature variation and partial shadow condition. The load used at the customer end has to be satisfied with the energy produced by PV source in renewable grid. The grid connected system shown in Figure 1 need the maximum load used by the customer, types of loads, energy produced by the PV source and state-of-charge (SOC) of battery bank. The generated power and the consumed power should match. If there is any mismatch in the power consumed for not using the loads or power hacked by the unauthorized customer, has to be identified and rectified by means of fuzzy-based energy management system.
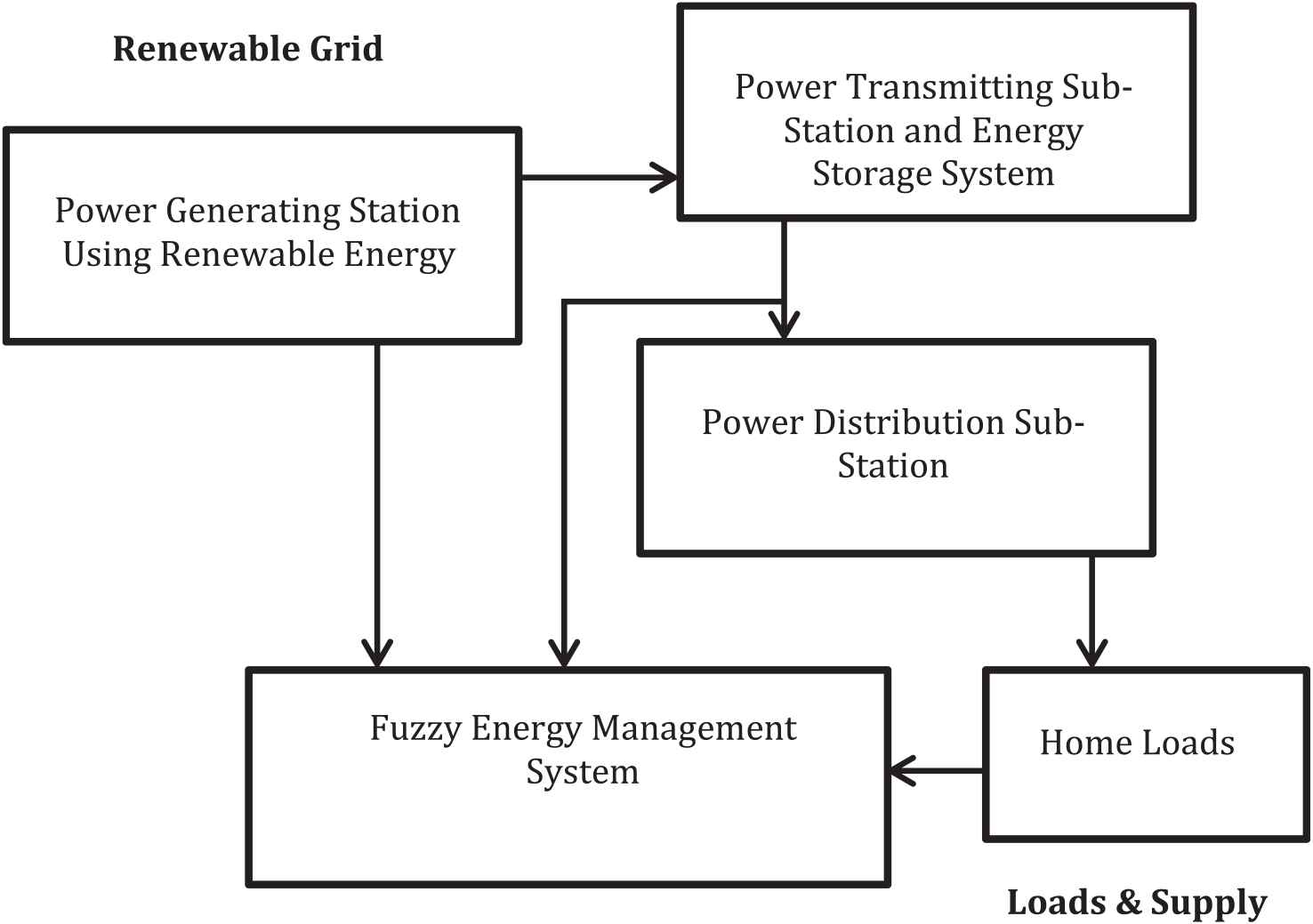
Block diagram representing dynamic regulation model with renewable source.
3. FUZZY-BASED ENERGY MANAGEMENT SYSTEM
The energy transition revolution has to meet the energy demand by various sectors for various loads. The energy generated by solar grid has to be transferred to transmission-distribution substation for the sake of customers to utilize. Also the energy loss and energy consumed by the unauthorized person has to be taken into account for better energy efficiency. In order to do this the power from solar-grid is supplied to various sectors in addition with the battery charging unit. Also control is given in fuzzy energy management system to identify the state of charge of batteries, power consumed, power delivered and also security has been checked for authorized and unauthorized customer in utilizing the generated power. The operation of fuzzy management system depends on PL as a minimum_power_element, PH as maximum_power_element, PC as power_consumed, PD as power_delivered, n as no_of_customer and PL as power_loss. The fuzzy-based energy management system will take decision based on J48 decision tree search algorithm for which the load will be powered and the customer using the source is authorized or an unauthorized. If the customer using the generated source is recognized to be unauthorized then the J48 decision tree algorithm transfer the data to the fuzzy management system to develop the control towards cutting down of the power. To have more precise control the fuzzy concept uses M-LP model and are as shown in Figures 2a and 2b.
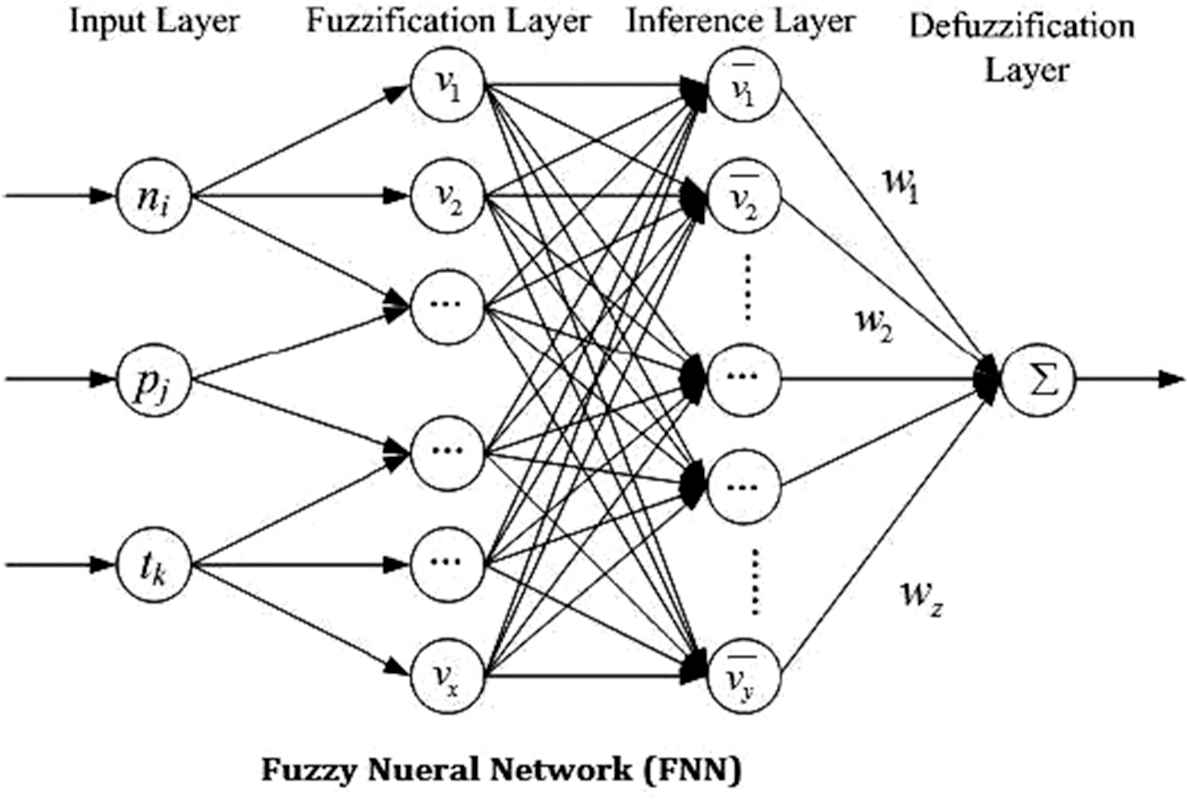
General fuzzy model.
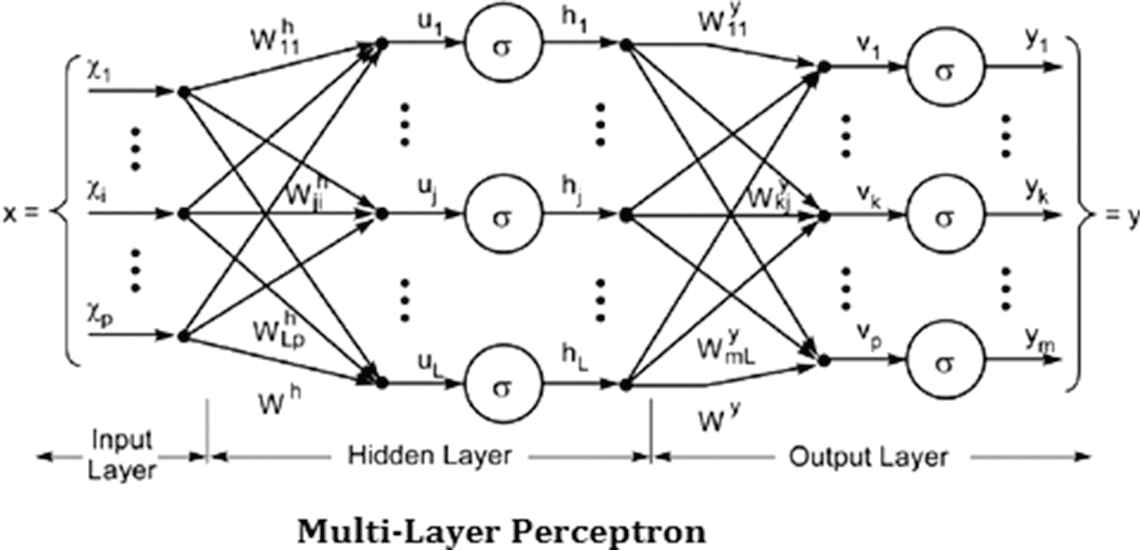
General fuzzy multilayer perceptron model.
4. J48 DECISION TREE
Electric power security in decision tree builds the classification and regression of various energy attacks in the form of tree structure. The energy-attack is collected as data set and this data set is break down into small small data set to identify the location where exactly the attack has happened. At the same time each data subset is associated with the decision tree and as a final result it lead to decision/root node and leaf node. The Figure 3 shows the J48 decision tree which can handle both numeric and categorical datas.
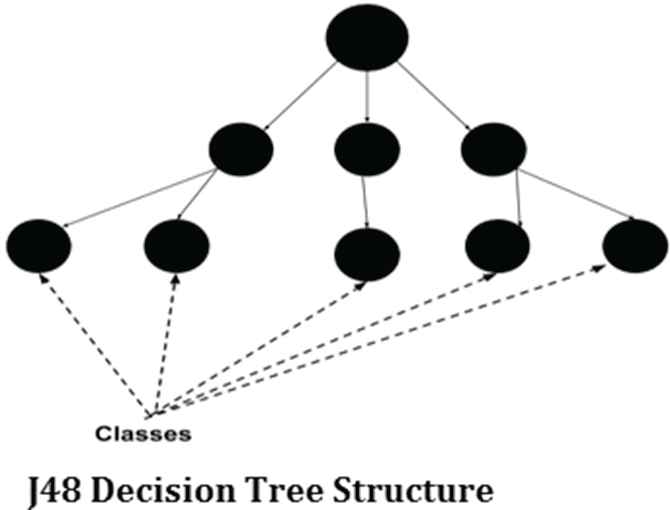
J48 decision tree.
This is the usual classifier to manage the supervised learning in fuzzy that gives prediction about the new unlabeled data.
5. MODIFIED J48 DECISION TREE ALGORITHM
Assign CADL is a root of the tree for the search process
Tree = {Elements of CADL} // where CADL consists of SMA, SDA, DMA, DDA
Calculation
Assign PL as a minimum_power_element // PL is a low range value
Assign PH as maximum_power_element // PH is a highest value
Assign PC as power_consumed // PC is a power consumption by various customers
Assign PD as power_delivered // PD is a power delivered by distribution station
Assign n as no_of_customer // n is the total no: of customer using various loads
Assign PL as power_loss // PL is a power loss in the line
PC = PC1 + PC2 + PC3 + ⋯ ⋯. + PCn
PD (Power_Difference) = | PD – PC | // Difference
Mid = loc (PD/2) // Mid - Selection of Middle range of power
Search process
If (Mid = e) // e – search element
Declare power_theft found
Else
If (Mid < e)
subtree = Tree(L) ⋯ Tree(Mid);
Tree = subtree;
Else
subtree = Tree(Mid) ⋯ Tree(H);
Tree = subtree;
End if
End if
6. SIMULATION TEST RESULTS AND ANALYSIS
The fuzzy-based energy management uses Mamdani's Fuzzy Logic Controller (FLC) approach which has got two fuzzy input i) PV Source temperature ii) Solar irradiance as input and output variable membership function is shown in Figure 4.
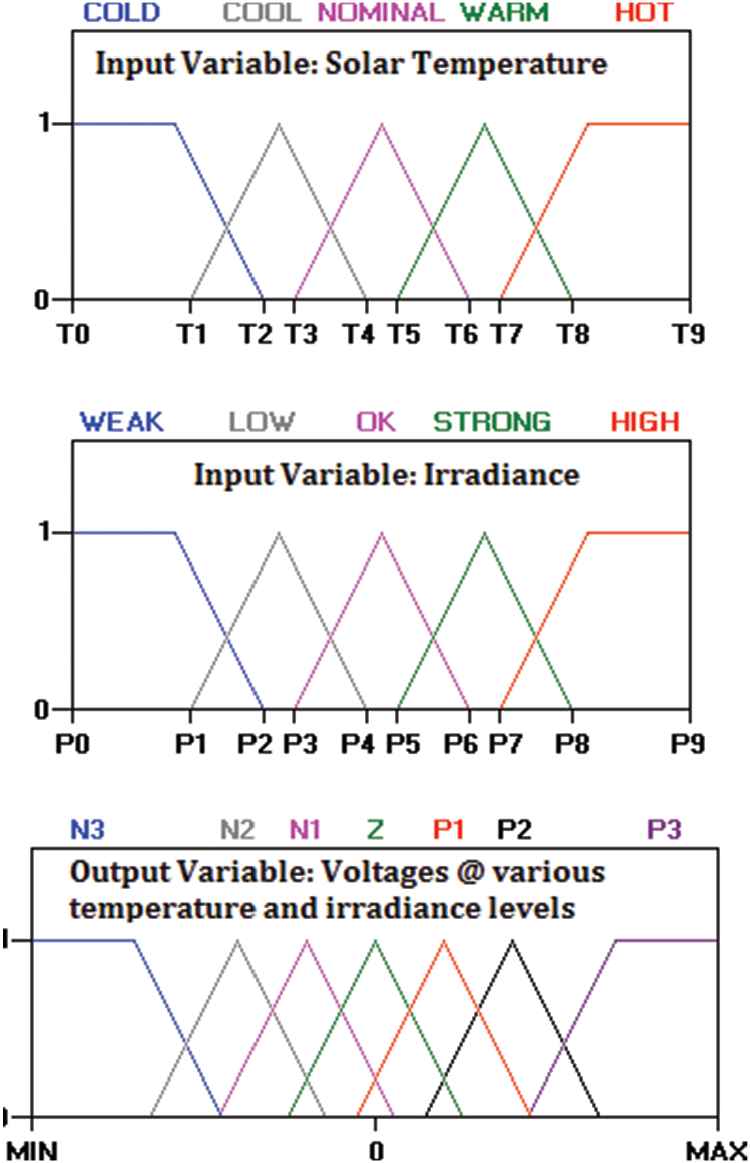
Membership functions of input and output variable.
After the definition of fuzzy variable and membership function, fuzzy-logic inference is utilized by using if-then statement in Table 1.
| Temperature/Climate | Cold | Cool | Nominal | Warm | Hot |
|---|---|---|---|---|---|
| Under | VL | L | M | H | VH |
| Normal | L | M | H | VH | VH |
| Over | M | H | VH | VH | VH |
Fuzzy rule.
6.1. Fuzzy Rule Inference Conditions
If temperature = under AND climate = Cold
THEN the probability of getting voltages of priority is only VL
If temperature = under AND climate = Cool
THEN the probability of getting voltages of priority is only L
If temperature = under AND climate = Nominal
THEN the probability of getting voltages of priority is only M
If temperature = under AND climate = Warm
THEN the probability of getting voltages of priority is only H
If temperature = under AND climate = Hot
THEN the probability of getting voltages of priority is only VH
If temperature = Normal AND climate = Cold
THEN the probability of getting voltages of priority is only VL
If temperature = Normal AND climate = Cool
THEN the probability of getting voltages of priority is only L
If temperature = Normal AND climate = Nominal
THEN the probability of getting voltages of priority is only M
If temperature = Normal AND climate = Warm
THEN the probability of getting voltages of priority is only H
If temperature = Normal AND climate = Hot
THEN the probability of getting voltages of priority is only VH
If temperature = Over AND climate = Cold
THEN the probability of getting voltages of priority is only VL
If temperature = Over AND climate = Cool
THEN the probability of getting voltages of priority is only L
If temperature = Over AND climate = Nominal
THEN the probability of getting voltages of priority is only M
If temperature = Over AND climate = Warm
THEN the probability of getting voltages of priority is only H
If temperature = Over AND climate = Hot
THEN the probability of getting voltages of priority is only VH
Figure 5 is the output from fuzzy Mamdani's FLC for fuzzy-based energy management system. In order to test the efficiency of the fuzzy-based energy management system and test the efficient of energy security, the energy demand by the customer according to the load and the power generated are taken as reference in fuzzy system. Again the power generation depends on the climatic conditions in the respective months. The analysis is done based on fuzzy rule and the output of the system at different moments are shown in Figure 6. The Figure 6 shows the output variation with reference to irradiance with and without energy management. Figure 7 shows the energy management strategy with and without fuzzy in polar chart and from the result it is observed that the energy management is efficient with a fuzzy-based controller.
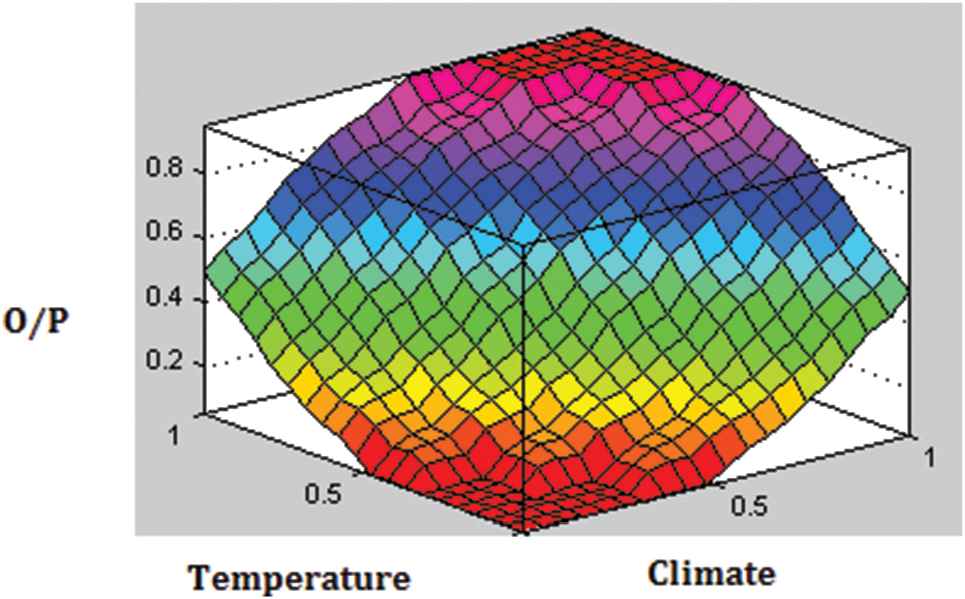
Generated surface of fuzzy-based energy management system.
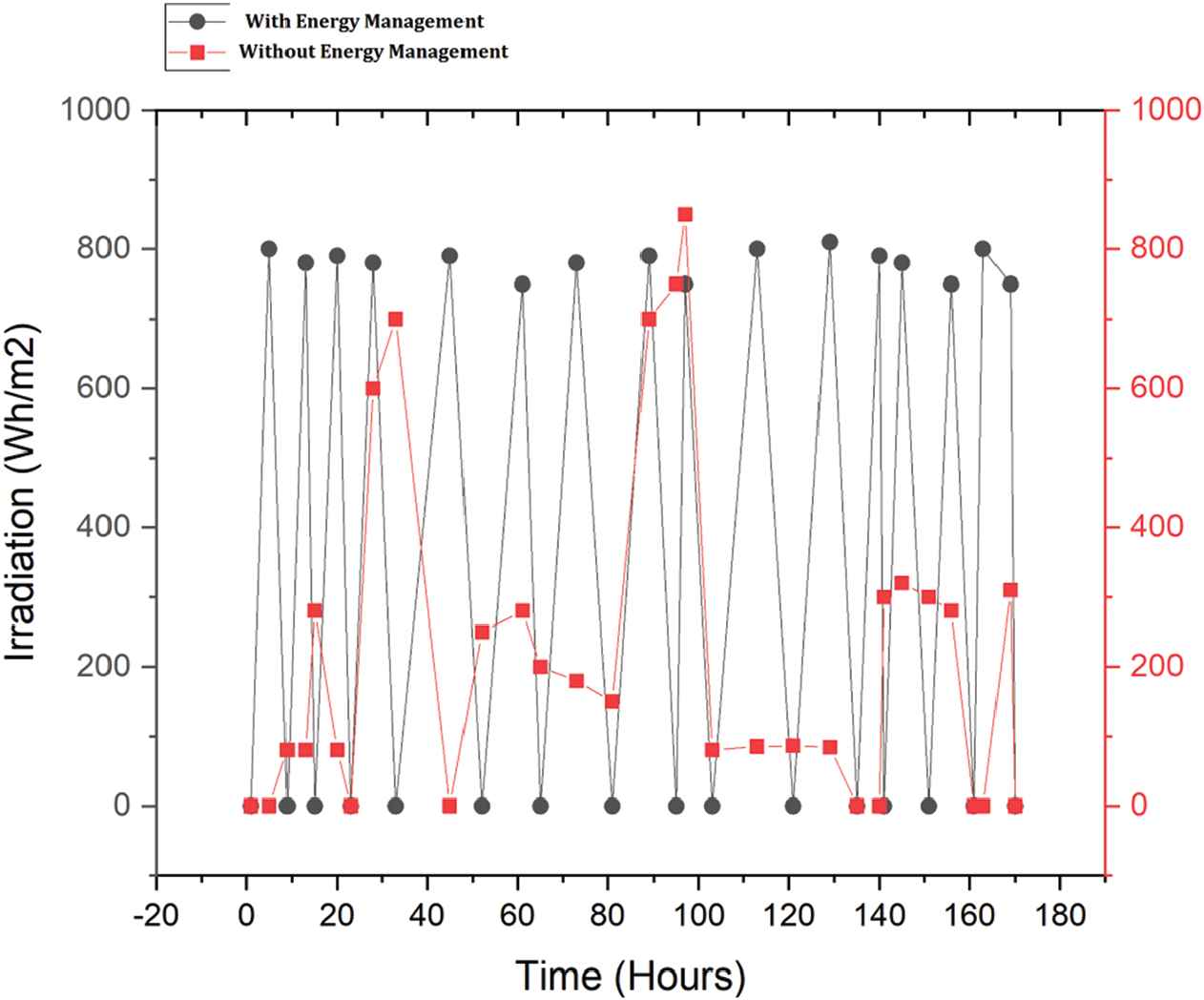
Solar irradiation at various time fact.
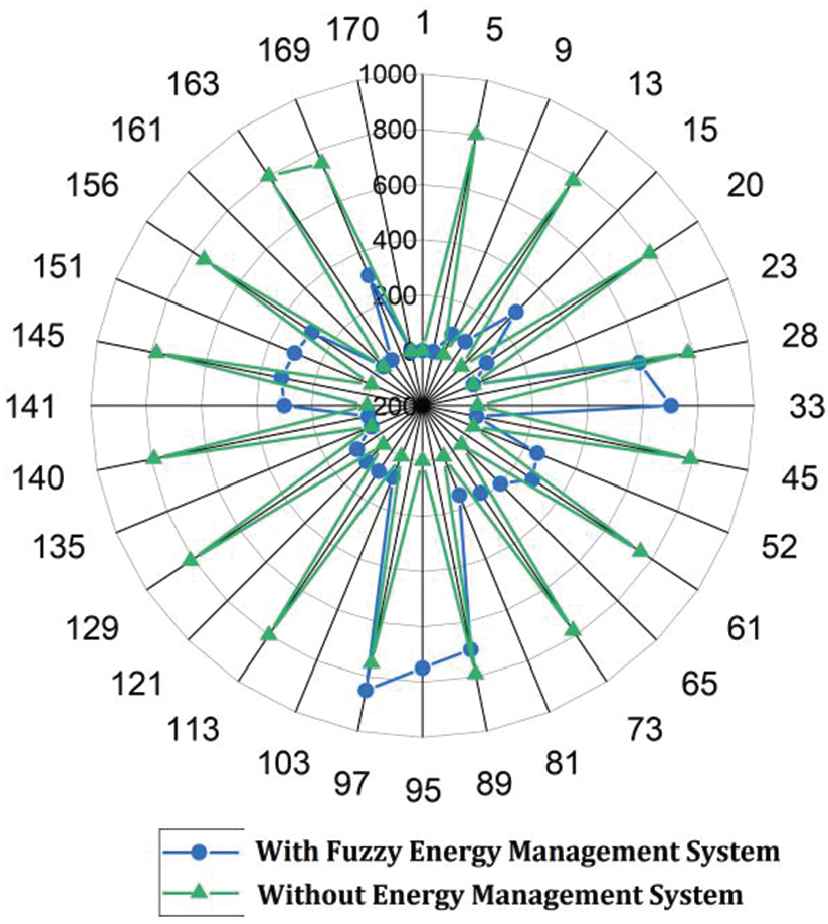
Energy consumption with and without energy management.
7. CONCLUSION
In this manuscript, J48 decision tree algorithm along with a fuzzy-based energy management technique is proposed for better power security and efficient energy management strategy. The energy management strategy is tested for various loads and the result takes load profile, voltage profile. The simulation proved that the optimal energy management is attained with the use of fuzzy as shown in Figure 7 at various loads. From Figure 7 it is very clear and understood that the energy consumption is reduced by controlling the loads with the use of fuzzy-based energy management system. The J48 decision tree algorithm is the best search algorithm used to identify the energy attack in the entire system.
CONFLICT OF INTEREST
The authors declare no conflict of interest.
AUTHORS' CONTRIBUTIONS
All authors contributed equally to the publication of this article with regard to the design of the target model, validation of the numerical model, parametric study, analysis and writing.
Funding Statement
There is no Funding for this manuscript.
REFERENCES
Cite this article
TY - JOUR AU - K. Ramya AU - Yuvaraja Teekaraman AU - K. A. Ramesh Kumar PY - 2019 DA - 2019/10/21 TI - Fuzzy-Based Energy Management System With Decision Tree Algorithm for Power Security System JO - International Journal of Computational Intelligence Systems SP - 1173 EP - 1178 VL - 12 IS - 2 SN - 1875-6883 UR - https://doi.org/10.2991/ijcis.d.191016.001 DO - 10.2991/ijcis.d.191016.001 ID - Ramya2019 ER -
